In 2014, mobile app usage accounted for 86% of time spent on mobile devices, up 6% from the year before, according to the Fire Eye report. As a result of user behavior changes, organizations are facing the following major mobile security challenges nowadays:
- Management of corporate mobile devices and BYOD
- Management and control of apps installment in the workplace
- Protection of sensitive data and critical information from online fraud and leakage
- Device ownership: IT people vs other roles within organization
Focusing on mobile devices and apps vulnerabilities and risks, we can flesh out the following critical threats:
- Malicious software, i.e. malware (often modular) targeting specific business needs. Examples: password cracking, banking modules, crypto currency modules, lockscreen modules, geolocation-based launchers
- New-generation viruses and worms targeting Internet of Things (IoT) enabled devices. Examples are: Symantec-discovered Linux.Darlloz that is capable of attacking a range of small devices such as home routers, set-top boxes and web cameras, as well as traditional PCs and mobile gadgets; Chameleon, a virus that infects Wi-Fi networks while moving through densely populated areas
- Mobile device breaches (through jailbreak, etc)
- Web-based attacks
- Network and system abuse, i.e. malicious encryption with data modification
- Resource and service availability abuse, i.e. spamming, botnet, overcharging SMS and calls
- Data loss and integrity
- Unsafe networks
- Backdoor to enterprise networks
- Social engineering attacks, i.e. phishing (e.g., only 24% of employees surveyed say they “never” accept invitations from strangers on social media sites, and 39% admit to opening emails that they suspected might be fraudulent or contain malware)
So, what are the key barriers to effective mobile security today?
- Lack of clear market definition and understanding within a global business community (e.g., only 39% of employees surveyed receive ongoing security awareness training or advice at their work more than once per year)
- Lack of buy-in from corporate leadership as a result of lack of understanding of modern security breaches and where they can lead
- Traditional, not mobile-focused, outlook on device and network security
- Device-centric vs user-centric approach
- Lack of security standards in innovative emerging niches such as wearable tech and IoT
Speaking about mobile device and apps security, I’ve outlined the following ways of avoiding / reducing threats and risks:
- Traditional access control, i.e. protecting devices with passwords and idle-time screen locking
- App provenance, i.e. user decides whether or not they want to use an app based on publisher’s identity
- Encryption, i.e. encoding data in such a way that only authorized parties can access it
- Isolation, i.e. limitation of app’s ability to access sensitive data and systems within the scope of permissions
- Permission-based access control, i.e. granting permissions and then limiting app’s ability to access device / system within the scope of permissions
Mobile platforms security

source: Symantec, 2015
As estimated in 2014:
- The number of Android vulnerabilities increased 188% compared to 2011
- The number of iOS vulnerabilities increased 262% compared to 2011
- 31% of the Google Play apps that have more than 50,000 downloads contained remote exploitable vulnerabilities
- There were 1,408 publicly distributed iOS apps that misuse enterprise provisioning profiles to deliver powerful attacks on iOS devices (660 in the United States alone)!
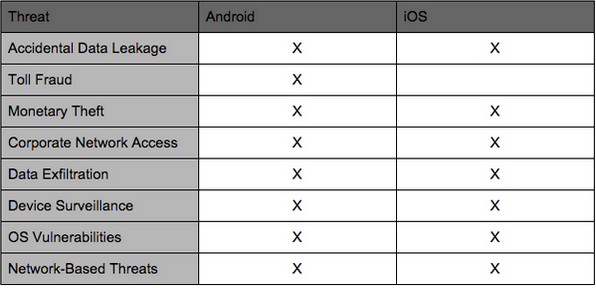
source: Lookout, Inc., 2015
It's clear as a day that Android is much more vulnerable to security breaches and data theft than Apple's iOS. Let’s review the most commonplace Android security threats.
Unlike Apple, Google uses a not so rigorous mobile security model allowing any software developer to build and publish apps anonymously, without inspection. That’s what makes Android a unique OS for smartphones, tablets, smart TVs and IoT enabled devices. Because Android is highly customizable and many hardware vendors modify the stock Android OS to better tailor software to specific pieces of hardware, it has become subject to security flaws and threats, with malware attacks surging from roughly 240,000 in 2013 to over 500,000 in Q1 2015.
Here are some of the Android security concerns that should capture your attention
- Third party app stores that contain more malware-ridden apps than the official Google Play
- Google Play is a safer marketplace than the 3rd party app stores; yet, even Google Bouncer malware tool doesn’t allow for 100% elimination of malware and adware infected apps
- Unlike Apple fans, Android users have traditionally been much slower to patch and upgrade to new versions of OS. The slow pace of updates means users remain stuck on older Android versions and are left vulnerable to data theft and malware as a result of bugs in the unpatched code.
- As mentioned above, Android is a highly fragmented OS that results in an unwanted side effect: fragmentation creates new ways for virus exploits that the stock Android OS doesn’t have. As the IoT movement is steaming up, the security concern surrounding fragmentation increases.
- Android is an open source OS which means every line of source code can be searched by professional or even amateur hackers to identify exploits.
- As estimated by Fire Eye’s recent research, more than 5 billion downloaded Android apps are vulnerable to remote attacks. The JavaScript-Binding-Over-HTTP (JBOH) vulnerability may be the riskiest one. A JavaScript binding method called add Javascript Interface is a common way of loading web content into an Android app. It’s also insecure. When an Android app invokes the method and loads the content from a web browser in WebView over HTTP, it opens the door for attackers to execute code remotely. (WebView is a way of showing web content in native Android apps). In other words, attackers can hijack the HTTP traffic to inject malicious content and links into the WebView code—gaining full control of the app running on the device. Of all popular Android apps with more than 50,000 downloads each, 31% are highly vulnerable. Of these apps, 18% fall into categories with potentially sensitive data such as finance, shopping, medical and productivity.
- App categories in Google Play that usually go the adware route are: entertainment, gaming, lifestyle, and communication. While adware is not in itself harmful, it often aggressively collects personal information from the mobile device it’s installed on: name, birth date, location, serial number, contacts, and browser bookmarks. Often, this data is collected without user consent.
Here’s what mobile app developers can do in the app ideation, design and development stages to reduce security risks for Android app users:
1. Embed security in your app design
As one game developer has once said, “I have become a big believer that you can't retrofit security”. Make sure to include your app security design to your mobile project spec prior to the actual development. For instance, relying too much on client-side data storage can open doors to numerous attacks, so such things should be planned up-front of your project start.
2. Learn how to code certain aspects of your mobile product in a secure way
Check out CERT guidelines for secure coding of Android apps.
3. Test each iteration of your Android app development
Once you’ve created your security design, embedded it in your project spec and learned the basics of secure coding, you should execute frequent code scanning (within each iteration, not just at the end of the project during your mobile app QA phase) and threats models to identify any design flaws and app vulnerabilities that will creep into your app. For instance, at Intersog we follow a secure design lifecycle that envisions a lot of mobile app testing. Our QA guys working on client projects document a clear set of security use cases and test it with design abuse cases. So, after each iteration, we define a security threat model which helps us identify the threat vectors, and then apply engineering mitigations and test each model for security issues. As part of frequent testing, we also monitor network traffic which can help us identify coding libraries and frameworks that perform insecure activities.
4. Encrypt all data that should be stored on the device
Poor encryption is one of the major issues facing Android apps. You may remember a story of Starbucks whose app left all user data unencrypted on the mobile device. Historically, developers have made such common mistakes as not encrypting data on the connection to the server and unsecured storage of authentication credentials. Developers should always keep hackers and their habits in mind and always think of app data in terms of security and encryption. Check out our mobile health app we’ve built for Video Medicine and learn how it exceeds HIPAA data safety compliance.
5. Shrink the opportunities for attacks
Instead of using broad frameworks, mobile developers should focus on minimizing the app functionality to only those capabilities that are really required by users. As such, they’ll be able to shrink the opportunities for attacks, or minimize the attack surface area of the application. Instead of trusting many certificates, developers can hardcode all trusted certificates into the software. Certificate pinning allows for elimination of the attack threats.
6. Use obfuscation
Obfuscation turns your code into indecipherable gibberish which helps raise your app’s security. According to Adrian Mettler, a development engineer on the FireEye mobile team, “If you make it difficult enough to reverse engineer your application, it may make it less likely that there is a trojanized version floating around somewhere”.
Check out how developers should protect iOS apps.
Sources: Information Week, 2015; Fire Eye, 2015; ZDNet, 2015; Lookout.com, 2015; TechBeacon, 2015






